Enabling Security Mitigations for Meltdown and Spectre on NI Linux Real-Time Controllers
Overview
Contents
- ARM-based Controller Mitigation Process
- Intel x64-based Controller Mitigation Process
- Advanced Programming
- Related Resources
ARM-based Controller Mitigation Process
In order to enable mitigations, the following steps must be taken.
- Install the 19.0 or later version of the specific controller’s device driver on the host computer.
- Upgrade the firmware of the controller to the 7.0 or later version by following Upgrading Firmware on my NI Linux Real-Time device.
- Format and Re-install software to the controller.
For example, if using the cRIO-9068, you would need to install NI-CompactRIO 19.0 and upgrade the firmware to get the mitigations.
Intel x64-based Controller Mitigation Process
In order to enable all mitigations, the following steps must be taken:
- Install the 19.0 or later version of the specific controller’s device driver on the host computer.
- Upgrade the Firmware of the controller to the 7.0 or later version by following Upgrading Firmware on my NI Linux Real-Time device.
Note PXI Linux RT controllers will not require a firmware update. Follow Installing Software on NI Linux Real-Time PXI Controllers to install software.
- Format and re-install software to the controller.
- Enable SSH from NI MAX and connect to the controller via SSH.
- Refer to Accessing the Shell on NI Linux RT Devices for help.
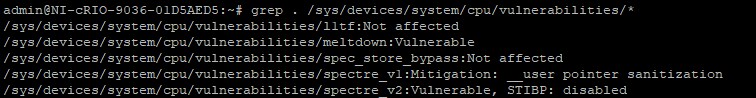
- (Optional) Confirm your target’s mitigations by observing the vulnerabilities files reported by running grep . /sys/devices/system/cpu/vulnerabilities/*
- Enable mitigations for all vulnerabilities in the INI file. This can be done using the nirtcfg utility in the shell.
nirtcfg --set section=SYSTEMSETTINGS,token=cpu.mitigations.disabled,value="False"
Vulnerability Status Name Section Token Value For NI Linux Real-Time 2022Q4 and Later All All SYSTEMSETTINGS cpu.mitigations.disabled FALSE For NI Linux Real-Time 2022Q4 and Prior Spectre Variant 2 Spectre_v2 SYSTEMSETTINGS spectre_v2.mitigations.disabled FALSE Spectre Variant 4 Spec_store_bypass SYSTEMSETTINGS spectre_v4.mitigations.disabled FALSE Meltdown Meltdown SYSTEMSETTINGS meltdown.mitigations.disabled FALSE Foreshadow L1tf SYSTEMSETTINGS l1tf.mitigations.disabled FALSE - Reboot the controller so your changes to take effect.
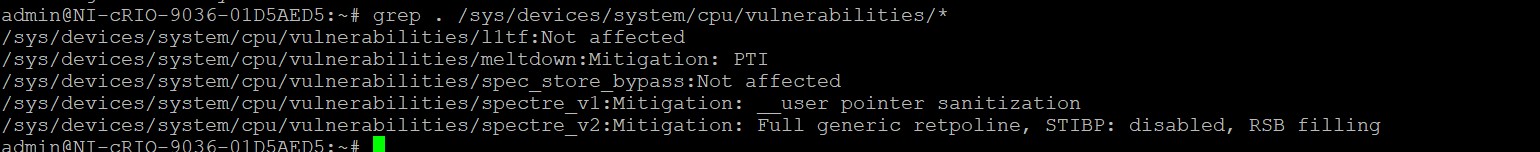
- (Optional) Confirm your new mitigation status by repeating step 5.
Advanced Programming
If you need to enable or disable specific mitigations for NI Linux Real-Time 2022Q4 and later, directly edit “/boot/runmode/cpu-mitigations.cfg” on the NI Linux Real-Time target.
If the cpu-mitigations file is named “cpu-mitigations.cfg.disabled” on your NI Linux Real-Time target you should first rename it to “cpu-mitigations.cfg”. Next you will need to replace “mitigations=off” in “cpu-mitigations.cfg”. Note that replacing mitigations=off will enable all mitigations by default. You will need to specify specific mitigations you want disabled in cpu-mitigations.cfg. For example, if you want to enable all mitigations but specifically disable spectre_v2 and meltdown mitigations you would update “cpu-mitigations.cfg” to the following:
set otherbootargs="${otherbootargs} spectre_v2=off pti=off"
Whenever you update “cpu-mitigations.cfg” you will need to reboot your NI Linux Real-Time target for the changes to take effect. For a complete list of mitigations please refer to the kernel parameter documentation for the kernel version you’re using on your NI Linux Real-Time target.