SELinux – LabVIEW RIOデバイスへのアクセス制御セキュリティに関する対応策
内容
インダストリアルIoT (IIoT) には、情報を相互で通信・共有できるような技術を組み込んだ物理的な対象物、システム、プラットフォーム、アプリケーションでネットワークを構築するという前提があります。産業用システムをつなぐこの巨大なネットワークは、データ解析を使い、ローカル処理と通信によってマシンをスマート化することで、工業パフォーマンスの向上と問題の解決を図ります。しかし、このアプローチには常にセキュリティ面での課題がつきまといます。
CompactRIOシステムなどのLabVIEW RIOデバイスには、IIoTのアプリケーションを保護する様々なセキュリティ機能があります。LabVIEW RIOデバイスのセキュリティ対策の包括的なリストについては、「RIOシステムのセキュリティベストプラクティス」を参照してください。Security-Enhanced Linux (SELinux) は、NI Linux Real-Timeベースデバイスにアクセス制御セキュリティポリシーを追加できるようにすることで、セキュリティ機能を拡張します。このドキュメントでは、SELinux管理の概要と高度な設定に関するリソースについてご紹介します。
SELinuxとは
SELinuxはそもそも、機密性と整合性の要件に基づいて情報を強制的に分離することで、悪意のあるアプリケーションによるダメージを最小限に抑えようというメカニズムを提供することを目的として開発されました。SELinuxとは、強制アクセス制御 (MAC) セキュリティポリシーをサポートするメカニズムを提供するLinuxカーネルセキュリティモジュールです。柔軟性のある強制アクセス制御 (MAC) を直接OSに提供することで、セキュリティに関する条件判断と、セキュリティポリシー自体を分離することが目的です。
SELinuxは、ユーザ、アプリケーション、プロセス、システム上のファイルに対するアクセス権および移行権を定義します。これらのやり取りをセキュリティポリシーによって管理することで、システムに損害を与える可能性のある悪意のあるアプリケーションからシステムを保護します。アプリケーションがファイルやリソースにアクセスしようとして、そのアクセスが従来のUnixの権限によって許可された場合、SELinuxはインストールされているポリシーが定義したセキュリティのコンテキストと照らし合わせて追加のチェックを実行し、リソースへのアクセスを許可するかどうかを決定します。
SELinuxポリシーとは
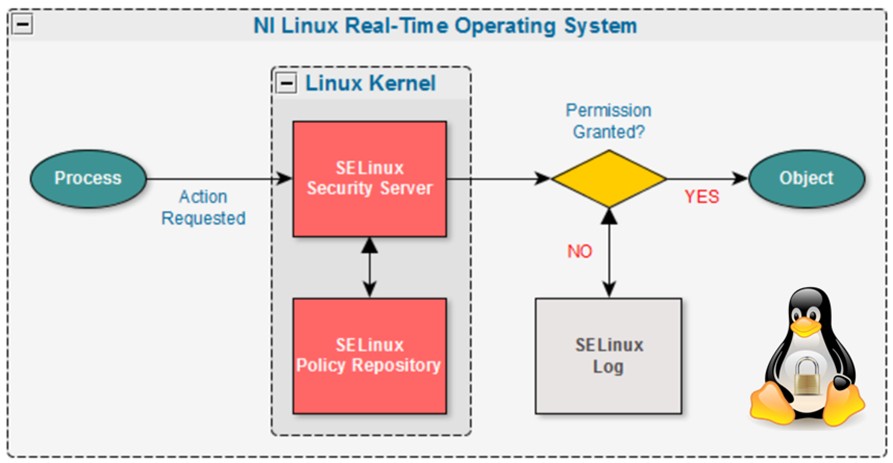
SELinuxポリシーには、プロセスとオブジェクトとの間のやり取りを管理するルールが含まれています。すべてのプロセスはラベル付けされ、それと同様にすべてのオブジェクトにもそれに関連したラベルが付けられます。これはポート、デバイス、さらにはホスト名についても同じです。つまり、SELinuxはポリシーを使ってラベル付けをするシステムで、ポリシーの中のルールに従って、ファイルなどのオブジェクトのラベルに対するプロセスのラベルのアクセスが制御されます。これらのルールを強制するのはカーネルであり、このアクションが強制アクセス制御 (MAC) と呼ばれています。
図1.Security-Enhanced Linuxの条件判断プロセス
SELinuxの最も重要な強制モデルはType Enforcement (タイプ強制) と呼ばれます。つまり、プロセスのラベルの定義がタイプに基づくということです。同様に、ファイルなどのオブジェクトのラベルもタイプに基づきます。たとえば、ホームディレクトリのオブジェクトはuser_home_tのようにラベル付けできます。これはタイプを表しており、この場合、ポリシーはこのラベルが付いたオブジェクトすべてをホームディレクトリのファイルとして扱う必要があるという意味になります。プロセスの場合も同様で、たとえば、Webブラウザはwebbrowser_tとして実行できます。これらのラベルに基づいてタイプ強制を用いることで、どのアプリケーションラベルがどのリソースラベルにアクセスできるかを指定できるようになります。たとえば、allow webbrowser_t user_home_t : file { read write };という指示は、webbrowser_tとして実行されているWebブラウザはuser_home_tとラベル付けされた、ホームディレクトリのファイルに対して読み取り/書き込みの権限があるという意味になります。このようにして、SELinuxは、ポリシーの定義で認められていないプロセスへのアクセスを拒否することで、オブジェクトおよびプロセスをそのタイプに基づいて分離します。
NI Linux Real-Timeターゲットには、標準ルールを含んだデフォルトの参照ポリシーが含まれます。このポリシーは、少数の広範囲に露出されたサービスに対するアクセスしか制限しません。つまり、ユーザのセッションは制限を受けず、妥当なユーザの操作が許可されます。しかし、これによって、組込ハードウェアターゲットで実行されているサービスのセキュリティは強化されません。ほとんどのアプリケーションはセキュリティのニーズの点において異なっているため、その差異に対応するためにSELinuxでカスタムポリシーを定義できるようになっています。 このツールに詳しくないユーザは、サードパーティのSELinuxインテグレータと協力して、特定のアプリケーション向けにカスタマイズされたセキュリティポリシーを定義することをお勧めいたします。
SELinux動作モード
SELinuxには、EnforcingとPermissiveの2つの動作モードがあります。通常運転の場合、SELinuxが搭載されたシステムはSELinuxを強制モードにして動作します。つまり、SELinuxポリシーは有効になっており、明示的に許可されていないアクセスは拒否されます。しかし、テストおよびデバッグ目的の場合には、SELinuxをPermissiveモードに切り替えることもできます。
Permissiveモードの場合、SELinuxを有効にしてシステムを実行できますが、同時に、本来は実行中のポリシーによって拒否されるすべてのアクセスが許可されます。つまり、Permissiveモードで実行されているシステムはSELinuxによって保護されないということです。 このモードの目的は、SELinuxが拒否したであろうアクセスを記録することです。これによって、管理者は、SELinuxをEnforcingモードにしたときにどういったことが起こるのか洞察を得ることができるのです。これが便利なのは、新しいポリシーを作成するときや、既存のポリシーで発生した予期せぬ拒否をデバッグするときです。
Enforcing – SELinuxセキュリティポリシーが強制される
Permissive - SELinuxセキュリティポリシーは強制されないが、SELinuxはデバッグおよびトラブルシューティングの目的で警告を表示する
リソース
SELinuxの設定方法および使用方法の詳細については、次のリンク先をご覧ください。
登録商標Linux®は、全世界における商標保持者Linus Torvalds氏から排他的ライセンスを受けているLMI (Linux Mark Institute) からの許諾により使用しています。ペンギンの画像の使用および修正はLarry Ewing and The GIMPにより許可されます。